Introduction
Service principal attacks are becoming more common and devastating. Two recent attacks included:
Midnight Blizzard Penetrates Microsoft Corporate environment
- January 2024
- By Russian state-sponsored group behind the SolarWinds attack
- Initial access via legacy test OAuth application in
- non-production tenant without MFA.
- NOT a zero-day or sophisticated malware.
- Leveraged full_access_as_app permission
- Read executive team emails
- Incursion lasted for months
Storm-0501 Compromises US Gov and Critical Infrastructure
- September 2024
- Ransomware group
- Vulnerability in service principals with Global Admin roles with MFA
- Reset on-prem passwords
- Misused Entra Connect Sync to penetrate cloud tenant
- Leveraged User Access Admin across all Azure subscriptions
- Deployed Ransomware
In January 2024, Midnight Blizzard—the Russian state-sponsored group behind the SolarWinds attack—compromised Microsoft's corporate environment. The initial access wasn't a zero-day or sophisticated malware. It was a legacy test OAuth application that hadn't been used in years, sitting in a non-production tenant without MFA. The attackers found it, compromised it, and used its full_access_as_app permission to read executive emails for months.
Eight months later, Microsoft reported on Storm-0501, a ransomware group targeting U.S. government and critical infrastructure. Their technique: identify service principals with Global Administrator roles that lacked MFA, reset the on-premises password, and let Entra Connect Sync hand them the keys to the cloud tenant. From there, they elevated to User Access Administrator across all Azure subscriptions and deployed ransomware.
These aren't edge cases. Field Effect observed a surge in application consent attacks in Q1 2024. Sixty percent of cloud threats now target identity and credential abuse. The pattern is consistent: attackers target non-human identities because they persist beyond password resets, often hold elevated permissions, and receive less monitoring than user accounts.
The challenge for defenders has always been visibility. When an attacker compromises a service principal, their first action is reconnaissance—enumerating users, groups, roles, and applications. This discovery phase was invisible from defenders’ point of view. Directory audit logs capture successful writes, not reads. By the time Midnight Blizzard's activity appeared in logs, they had already mapped Microsoft's environment. Now there’s good news for defenders as Microsoft’s Graph API aims to increase visibility into these attacks.
GraphAPIAuditEvents: Closing the Gap
Microsoft's GraphAPIAuditEvents table in Defender XDR Advanced Hunting is built to change this. Available in preview for P2-licensed customers, it captures all Graph API requests—reads, writes, successes, and failures. Each record includes the source IP, HTTP method, response code, and a token identifier linking activity to specific authentication sessions.
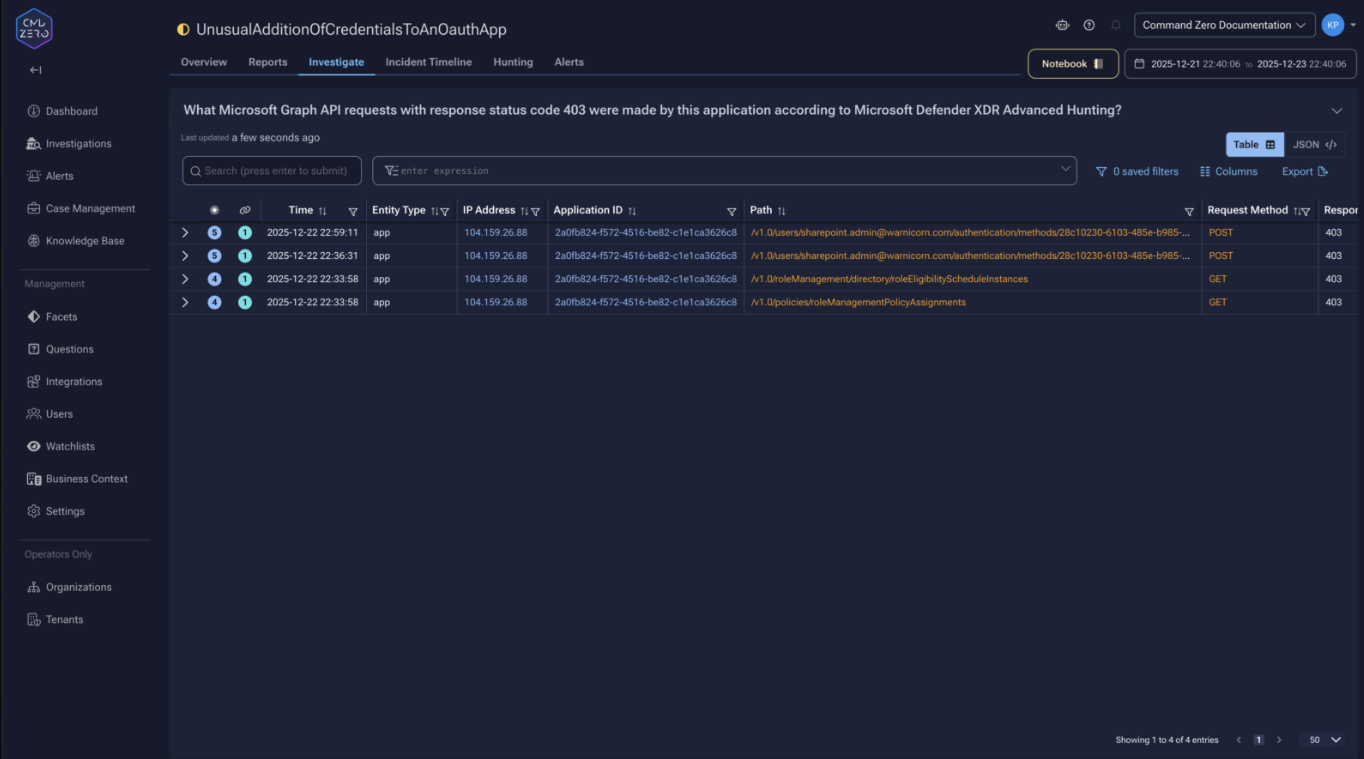
This transforms service principal investigations. Analysts can see enumeration: hundreds of GET requests to /users, /groups, and /directoryRoles that precede an attack. They can see probing: 403 responses revealing what an application attempted but couldn't access. They can trace a token from authentication through every API call it made.
New Investigation Content for Service Principals
Command Zero has released our first investigation content leveraging GraphAPIAuditEvents. This includes questions for analyzing Graph API activity by application, by source IP, and by authorization token—with automatic correlation across the identifiers that make manual investigation tedious.
We've also built automated investigation facets for two attack patterns that appear repeatedly in incident reports: service principal ownership abuse (the privilege escalation technique Semperis documented in 2024) and OAuth consent grant abuse (the technique Midnight Blizzard used against Microsoft).
Walkthrough: Investigating Ownership Abuse
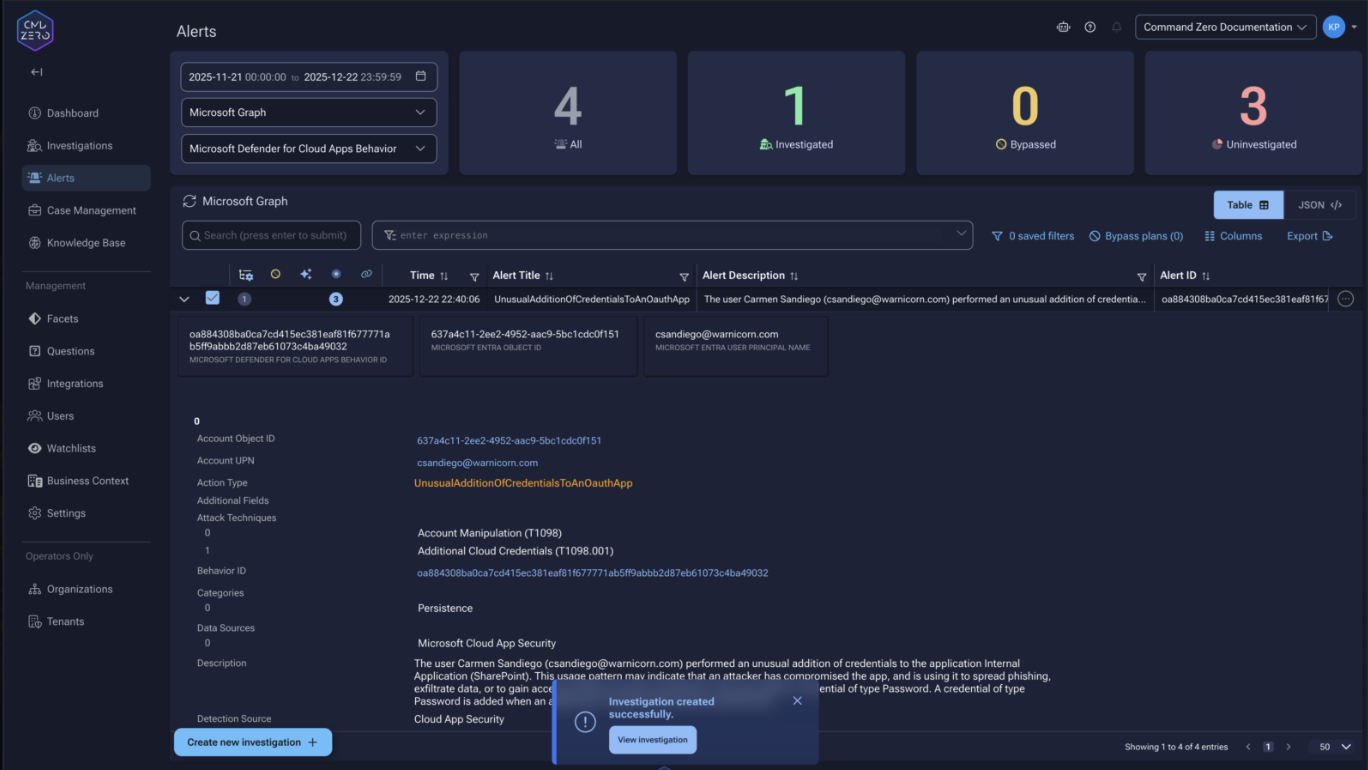
Consider a Defender XDR alert: "Unusual addition of credentials to an OAuth app." The analyst needs to determine whether this was legitimate or the opening move of a privilege escalation attack.
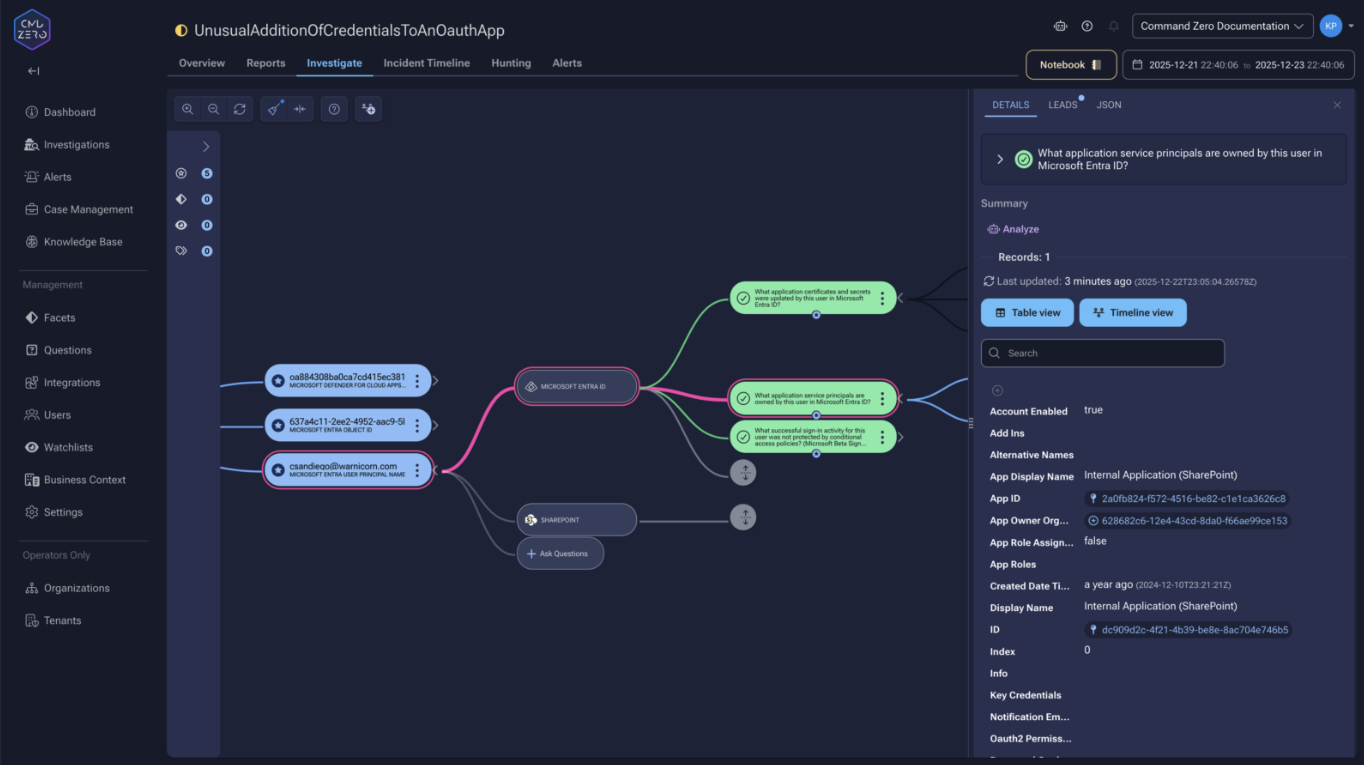
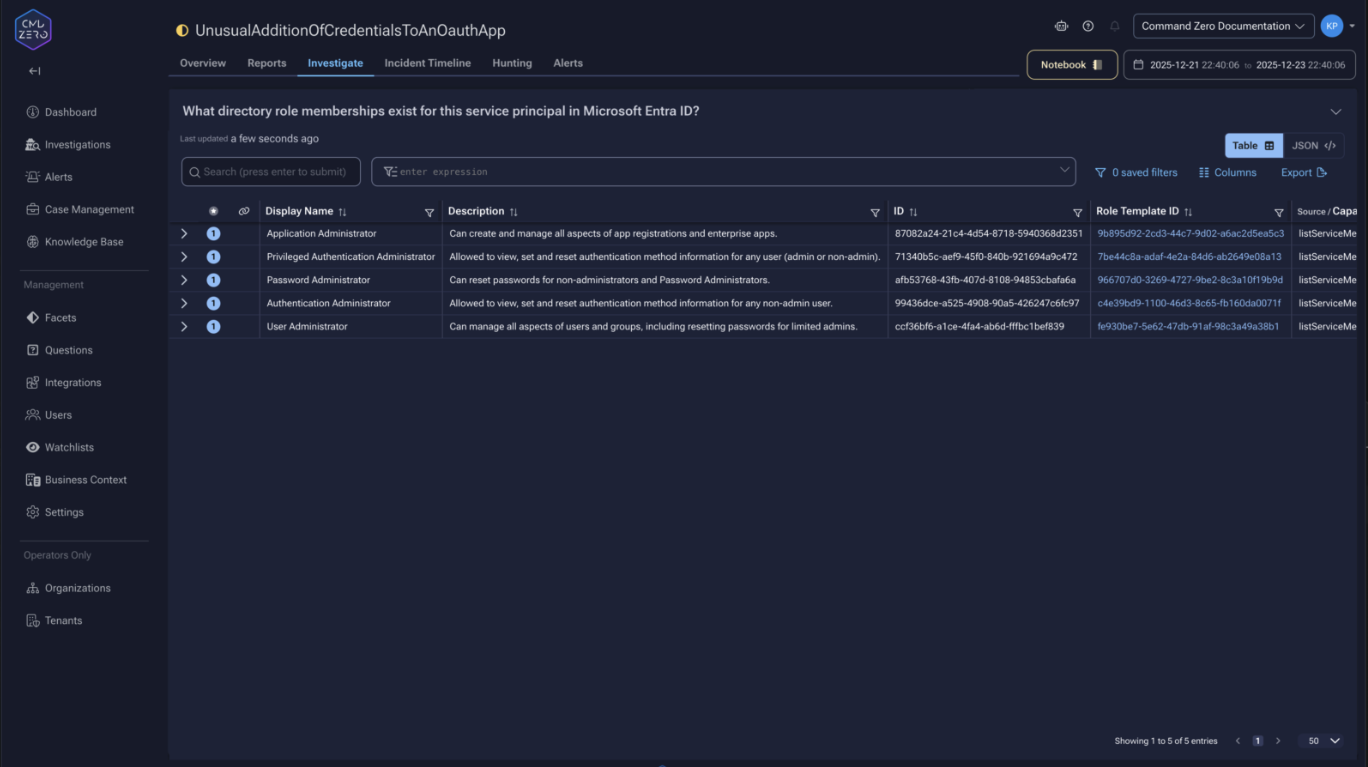
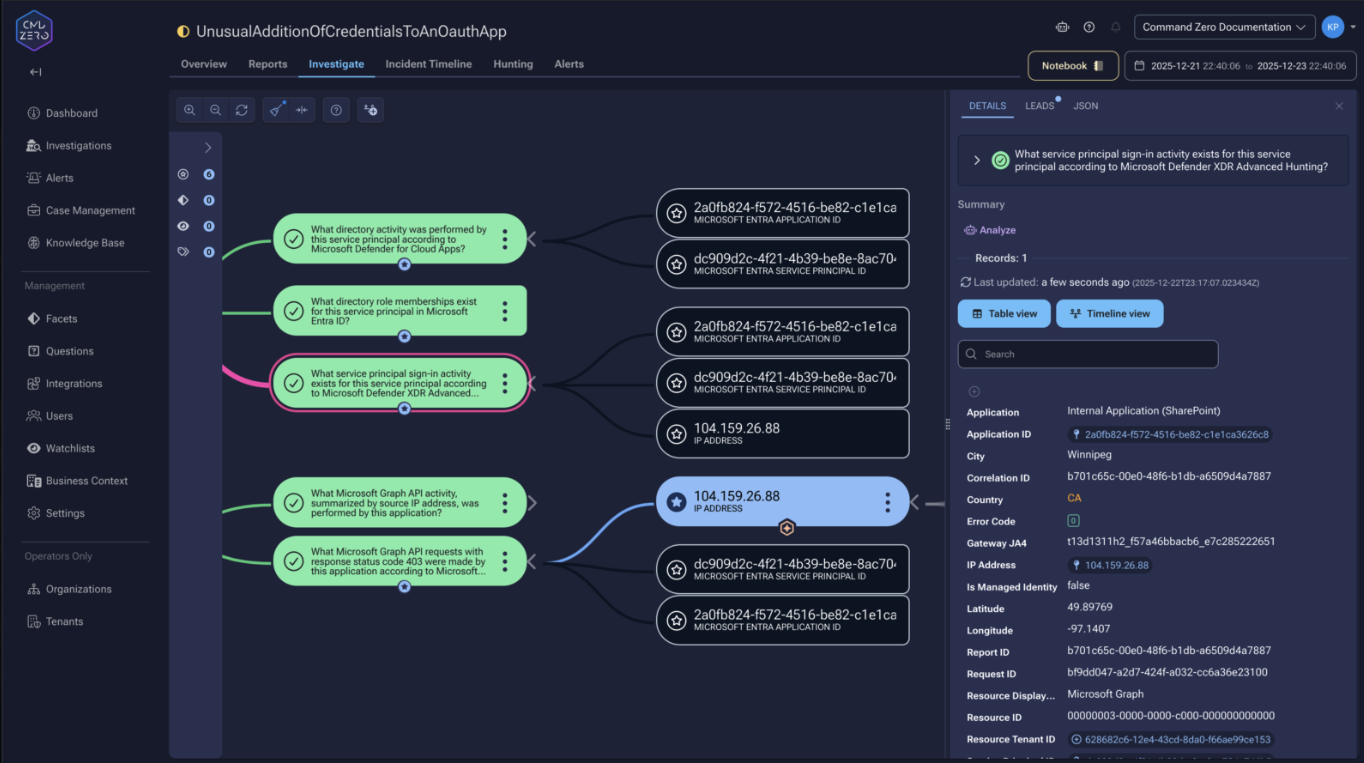
The investigation identifies the application and enumerates its owners—in Entra ID, owners can add credentials without additional permissions. Directory role memberships reveal the blast radius: if the service principal holds Privileged Authentication Administrator, an attacker could reset any password, including Global Administrators.
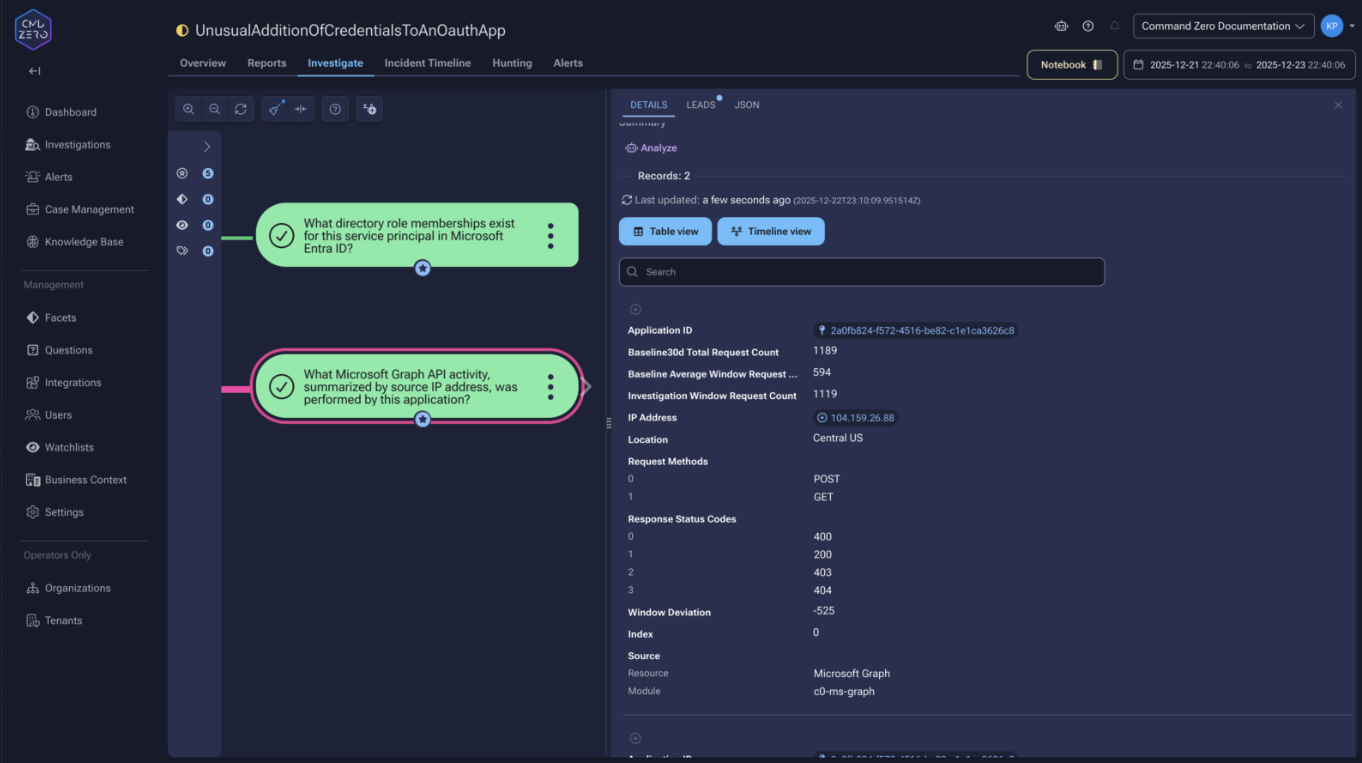
The Graph API activity summary shows what the application has done. Results aggregate by source IP with 30-day baseline comparison. If the application typically operates from known cloud infrastructure but suddenly appears from a residential ISP in an unexpected country, that’s a meaningful signal. HTTP methods and response codes indicate whether it was reading, modifying, or probing permission boundaries.
Service principal sign-in logs provide authentication context, with token identifiers that correlate to specific API activity. Defender for Cloud Apps shows directory actions performed. The investigation checks whether identified owners added credentials, confirming the abuse mechanism.

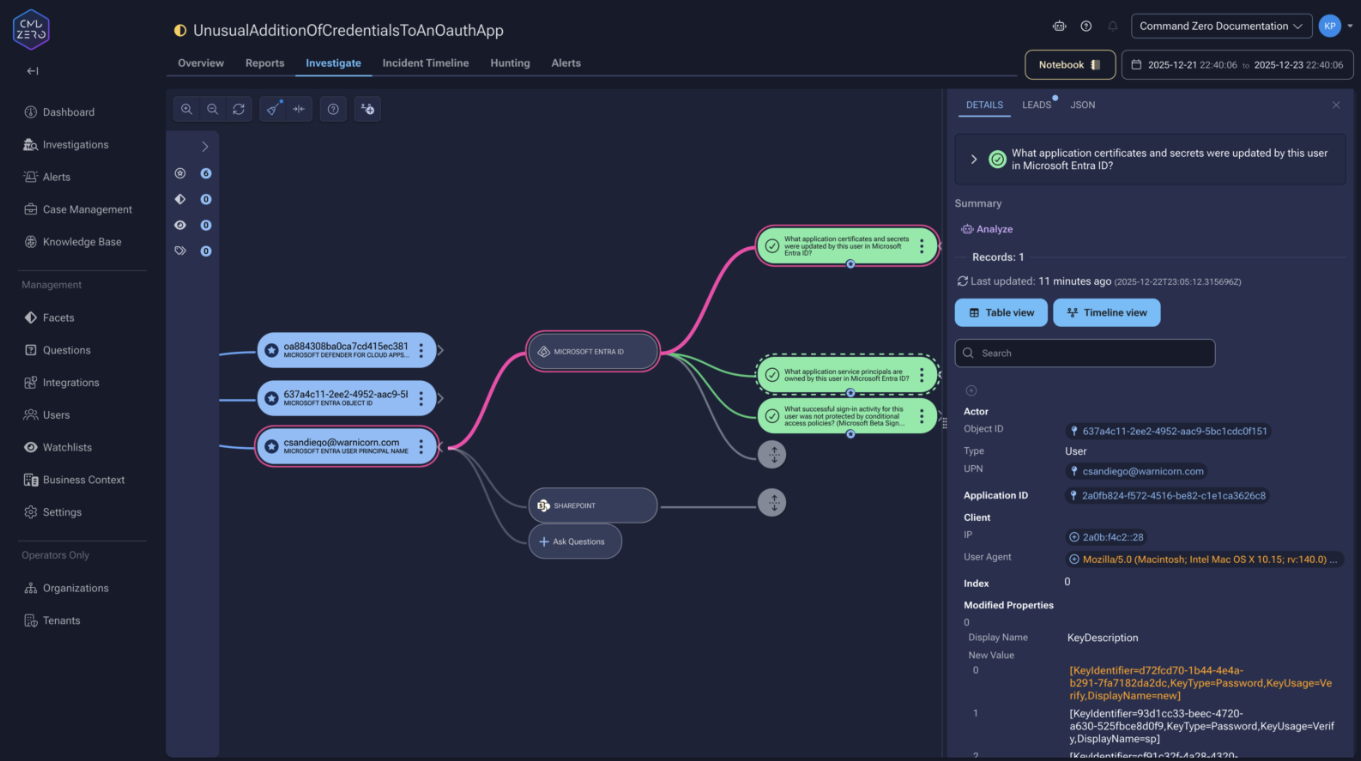
Reviewing The Complete Attack Chain
Before GraphAPIAuditEvents, an ownership abuse investigation had gaps: alert fires for credential addition, then nothing, then audit logs show a Global Administrator password was reset.

With GraphAPIAuditEvents, the full sequence surfaces: credential added, service principal authenticates from unfamiliar IP, 800+ GET requests enumerate users and roles over 12 minutes, POST creates a Temporary Access Pass for a Global Administrator, audit log confirms the reset. The reconnaissance that Midnight Blizzard conducted invisibly for months would now be visible within the investigation window.
Increasing Visibility Within Expanding Attack Surface
Storm-0501 found a service principal with Global Admin. Midnight Blizzard found a forgotten OAuth app with Exchange access. Both attacks succeeded because non-human identities weren't receiving the same scrutiny as user accounts.
Organizations deploy more applications and integrations every year. GraphAPIAuditEvents closes the visibility gap for investigating them. Command Zero automates the correlation across data sources that previously required hours of manual work.
Service principal attacks aren't theoretical—they're in the threat reports. The APIs to investigate them are now available.
Book a demo today to see how Command Zero can help make the most of Graph API in your environment to tackle service principal attacks.








